Tracking 2022 Cyber Threat Trends
by Nick Kael
Posted on April 5, 2022
In 2021, cybercrime continued the precipitous increase that began in 2020, triggered by COVID-necessitated work-from-home, and inflicting trillions of dollars of damages on businesses, organizations and individuals worldwide.
In its recently issued 2022 Threat Intelligence Index, IBM analyzed billions of data points from cyberattacks conducted in 2021. All of the information contained in the 59-page report is interesting, and much of it is alarming. In this post we highlight a number of key findings.
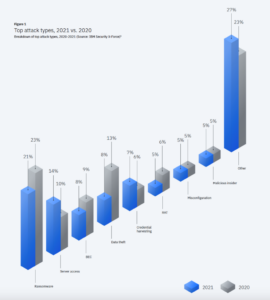
Top Five Cybercrime Objectives
The top five attack objectives in 2021 were:
- Ransomware (21%) – Topping the list for over three years.
- Server access (14%) – In these are attacks, the ultimate goal was uncertain, but it could have been stealing data, injecting ransomware, or something else.
- Business email compromise (BEC) (8%) – BEC attacks, which involve using the identity of a senior employee of the victim’s organization get them to wire money or divulge information, were down compared to 2020, perhaps due to increased use of multi-factor authentication.
- Data theft (8%)
- Credential harvesting (7%) – the growth of credential harvesting attacks highlights increasing specialization in the cybercrime world. The cybercriminals who steal the credentials don’t necessarily launch attacks themselves, but rather sell credentials to others.
Ransomware
The percentage of attacks categorized as ransomware decreased slightly in 2021, from 23% in 2020 to 21%. The number of ransomware attacks, however, held steady – other types of attacks increased more, which the IBM team attributes to intense of law enforcement heat on ransomware gangs.
Five Stages of a Ransomware Attack
Ransomware attacks are defined by their end goal, as mentioned above. But deploying the ransomware is just the final step of a multistage process that entails criminal activity at every step.
IBM’s team has identified five stages that characterize almost all ransomware attacks:
- Initial access. The attacker finds a way into the target network, typically through phishing or by exploiting a software vulnerability or a remote access protocol such as RDP.
- Post exploitation. Once in, the attacker deploys malware droppers or intermediary remote access tools (RATs) which are, in turn, used to deploy offensive cyberattack tools.
- Understand and expand. Attackers don’t generally launch attacks immediately and indiscriminately. Instead, they explore and study the network, and seek additional credentials to give them the capability to move laterally.
- Data collection and exfiltration. Cybercriminals are no longer content with only collecting ransom. In this stage, they steal company data and identify what is most valuable before encrypting it, so they can then either sell it to third parties or hold it for further extortion (“pay up, or we’ll release your sensitive data”).
- Ransomware deployment. The attackers almost always use a domain controller as the way to distribute their ransomware payload.
Triple Extortion
One of the most worrying trends noted by the IBM researchers is a move to “triple extortion.” With triple extortion, attackers use a three-pronged threat:
- The basic ransomware. The victim’s data is encrypted, and they are offered a decryption key for a price.
- Extortion based on data exfiltration. The attackers threaten to sell or publish sensitive data they stole from the company’s network. Of course, paying is no guarantee that they won’t sell or expose the data anyway.
- Extortion based on a threatened Distributed Denial of Service (DDoS) attack against the company. Even if an organization has backups and is well-prepared to recover from having their data encrypted, they are unlikely to be able to handle two types of malicious attacks simultaneously.
IBM also reported that attackers are increasingly threatening the victim’s business partners with exposure of their data to increase pressure on victims to pay up.
Top Five Infection Vectors in 2021
Infection vectors represent the first stage – that is, the initial access – for attack objectives, like ransomware. Last year’s top five infection vectors were:
- Phishing (41%)
- Vulnerability exploitation (34%)
- Stolen credentials (9%)
- Brute force (6%)
- Remote desktop (4%)
A social engineering campaign simulation, in which IBM’s X-Force team sent emails masquerading as phishing attacks to unsuspecting users, yielded a shocking 17.8% clickthrough rate. Worse yet, when they added “vishing” (voice phishing, or phone calls) to the phishing campaign, the clickthrough rate rose to 53%. These high success rates – from the point of view of the cybercriminals, of course – go a long way to explaining why phishing has become the dominant infection vector for ransomware attacks.
Phishing is a high volume, low frequency approach, with a constant stream of sites that are deployed, gather credentials from or spread malware to a small number of victims, and are quickly shut down by hosting providers. As a moving target, phishing is notoriously difficult to tackle.
Implications for Cybersecurity
These trends have numerous implications for planning defense. For instance, understanding the stages of ransomware attacks enables organizations to implement countermeasures that might slow or stop the attack at each stage. Clearly, however, blocking initial access entirely is the most desirable approach.
Fortunately, there are effective ways to protect against each of the five primary infection vectors for initial access.
Relying on user training to protect against phishing attacks may reduce the number of clicks but is not a reliable protective strategy. The best way to protect against phishing is with Zero Trust based solutions, such as Remote Browser Isolation (RBI). Choose an RBI solution that opens recently created sites in read-only mode, so that users cannot enter credentials. RBI also prevents malware from infecting your network even if a user clicks to an infected website, since no website content reaches the endpoint.
Avoiding falling victim to a vulnerability exploit is considerably more complex, since each vulnerability is different. The first and most obvious is to ensure that security updates and patches are promptly installed. This is, of course, easier said than done: Keeping up with the constant stream of patches and updates is a challenge even for organizations with large IT teams, and most teams can barely keep up with the most pressing tasks. Patching can also be complex, since one change may have numerous ripple effects that break working processes. For these reasons, many companies fall victim to attacks via vulnerabilities that have been known for months or longer.
RBI also protects against vulnerabilities that impact websites and apps, such as the recent spate of use-after-free vulnerabilities that allow malicious code to be injected into endpoint memory that has been freed by a website or web app. RBI prevents websites and apps from interacting directly with resources from the user device, so no malicious code can reach them via the web.
Multi-Factor Authentication (MFA) is the best way to protect against breaches via stolen credentials. MFA isn’t foolproof – dedicated hackers have been able to foil MFA and even biometric-based MFA – but it will stop the vast majority of credential theft-based attacks.
Vulnerabilities in remote desktop access solutions such as RDP, RDS and VPNs have been massively exploited since the rapid coronavirus-triggered shift to work from home. Alternatives such as Zero Trust Network Access (ZTNA) provide a much greater level of security.
The later stages of ransomware attacks, in which attackers move laterally to explore networks to find weak spots and to collect and exfiltrate data, can be foiled by deploying microsegmentation and policy-based least privilege access techniques to sharply limit lateral movement on the company’s servers and access to sensitive data.
Conclusion
The digital world is an increasingly dangerous place, with cyberattacks on the rise, ransomware demands rising, and easy-to-use tools such as ransomware-as-a-service lowering the technology bar and expanding the pool of cybercriminals.
Traditional perimeter-based cybersecurity has been rendered obsolete by the shift to remote work and cloud-based resources. Protecting today’s complex, hybrid IT environment calls for a shift to a comprehensive Zero Trust approach, such as ZTEdge, a state-of-the-art Secure Access Service Edge solution designed specifically for the needs of midsize enterprises.
About Nick Kael
A cybersecurity expert with over 20 years of experience in web technologies, architecture, infrastructure, networking and dev environments, Nick is responsible for solution management, technology strategy and technology partnerships. Nick was previously Symantec Group CTO for Global Service Providers, following his tenure as Director of the Chief Architect Team for Channel and Service Providers at Zscaler and an earlier position in the Symantec CTO organization. His certifications include CEH7, CCSK, BCCPP, Bluecoat Blue Knight, MCSE + Security, CCDP, CCNA, CCSA, VTP5 and VTSP5.Recent Posts

Air Gapping Your Way to Cyber Safety
Physically air gapping enterprise networks from the web is a great way to protect operations, keep data safe … and squelch productivity. Virtual air gapping is a better approach.

Motion Picture Association Updates Cybersecurity Best Practices
The MPA recently revised its content security best practices to address, among other challenges, the issue of data protection in the cloud computing age.

FTC Issues Cybersecurity Warning for QR Codes
QR codes on ads are a simple way to grab potential customers before they move on. No wonder cybercriminals are using QR codes, too.