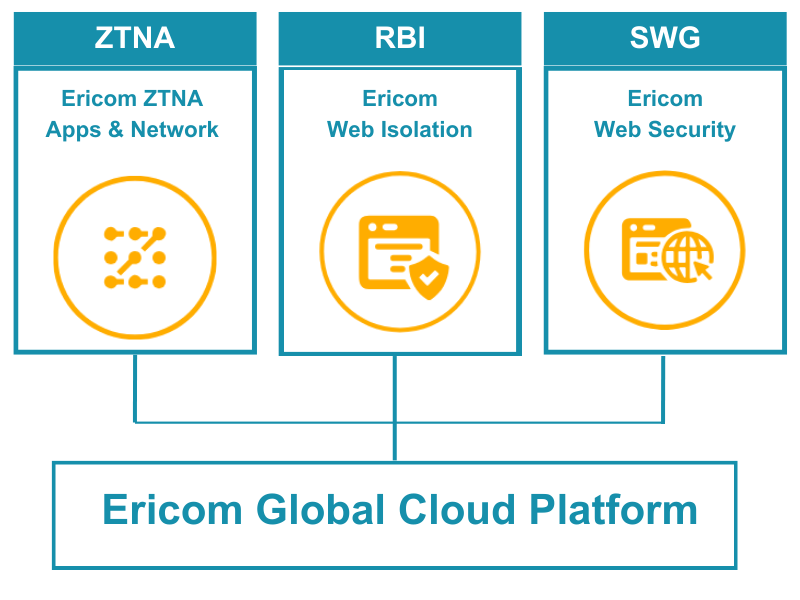
Deliver the Zero Trust Security Solutions Customers Need Now
Rapidly grow your business with simple, yet powerful, proven Zero Trust security solutions that secure your customers’ environments. Ericom offers three Zero Trust solutions that Gartner’s Network Security Hype Cycle puts on the “Slope of Enlightenment” – ZTNA, RBI, and SWG. Your customers have the budgets allocated for these offerings and Eric0m helps you deliver the most cost-effective and affordable solutions on the market. Ericom designed the Ericom VAR program to provide excellent implementation assistance, technical support, and strong partner margins.
Ericom ZTNA, Apps and Network
Zero Trust Network Access
Integrated IAM & MFA
Automatic Policy Generation
Least Privilege Access
Ericom ZTNA, Apps and Network makes it easy to connect users, even 3rd parties, to any app or resource, regardless of location (cloud or on-prem). No network reconfiguration is required, and you customers can integrate with the identity solution they already use or utilize ZTEdge’s built-in identity capabilities.
With our patent-pending Automatic Policy Builder, your customers can easily set granular access policies, and let the solution analyze network traffic to create recommended configurations.
Dashboards provide continuous fine-grain visibility on user behavior and network traffic so you can help your customers:
- Easily connect users to apps, boosting productivity and accelerating digital transformation initiatives
- Save time on manual configuration and administration, freeing up IT resources
- Implement 1:1 microsegmented access secures an organization’s apps and reduces lateral movement and ransomware risks
Ericom Web Isolation
Stop Malware
Phishing Prevention
Sanitize Downloads
Prevent Data Loss
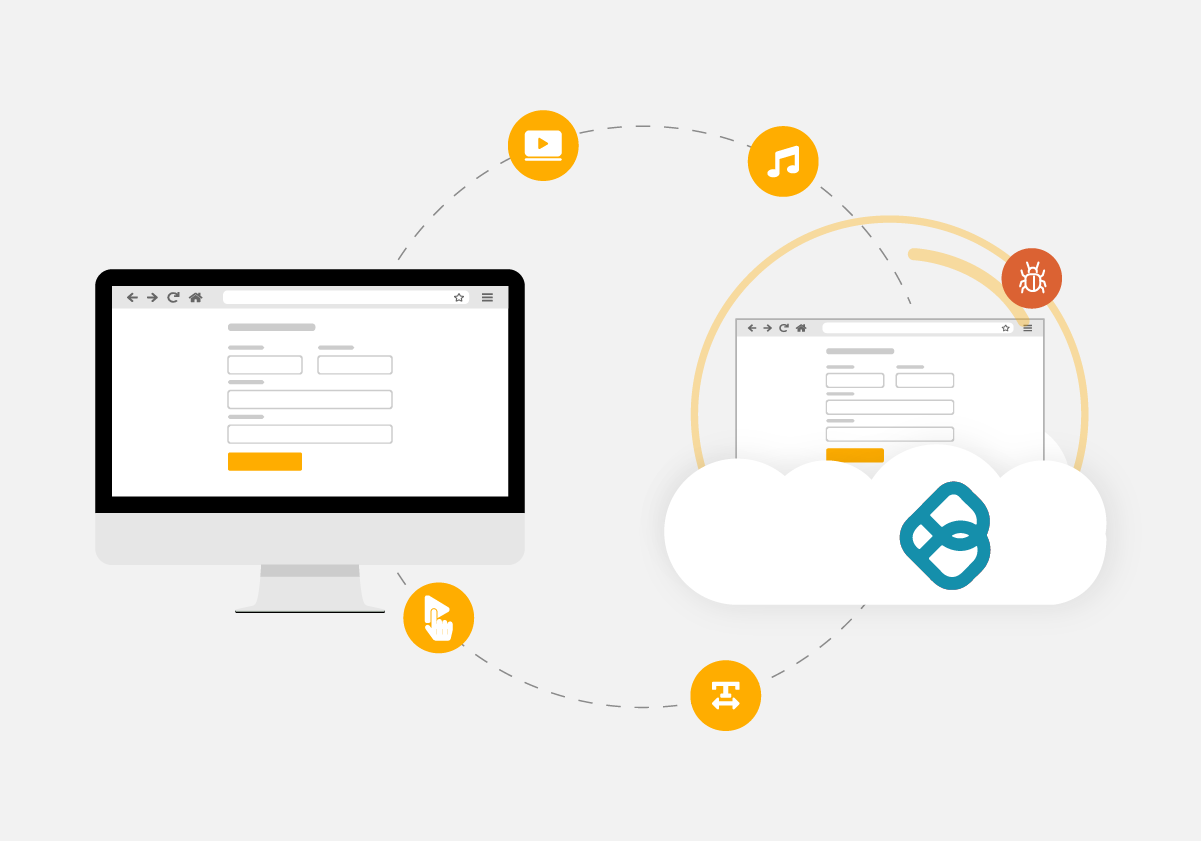
Ericom Web Isolation uses RBI to render website content in virtual browsers located in cloud-based containers.
Only safe rendering information is sent to users’ regular web browsers, provides a natural, fully interactive user experience, while safeguarding devices and networks from malware hidden on websites – even advanced zero-day ransomware.
- Block weaponized downloads/attachments with Content Disarm and Reconstruction (CDR) capabilities that remove malware from web downloads and email attachments
- Prevent malware, ransomware, and zero-day web threats from infecting user devices and networks
- Isolate suspected phishing sites and render them as read-only to prevent credential theft with next-gen email security
- Stop sensitive data from being stored in browser caches and limit data sharing on websites and cloud apps
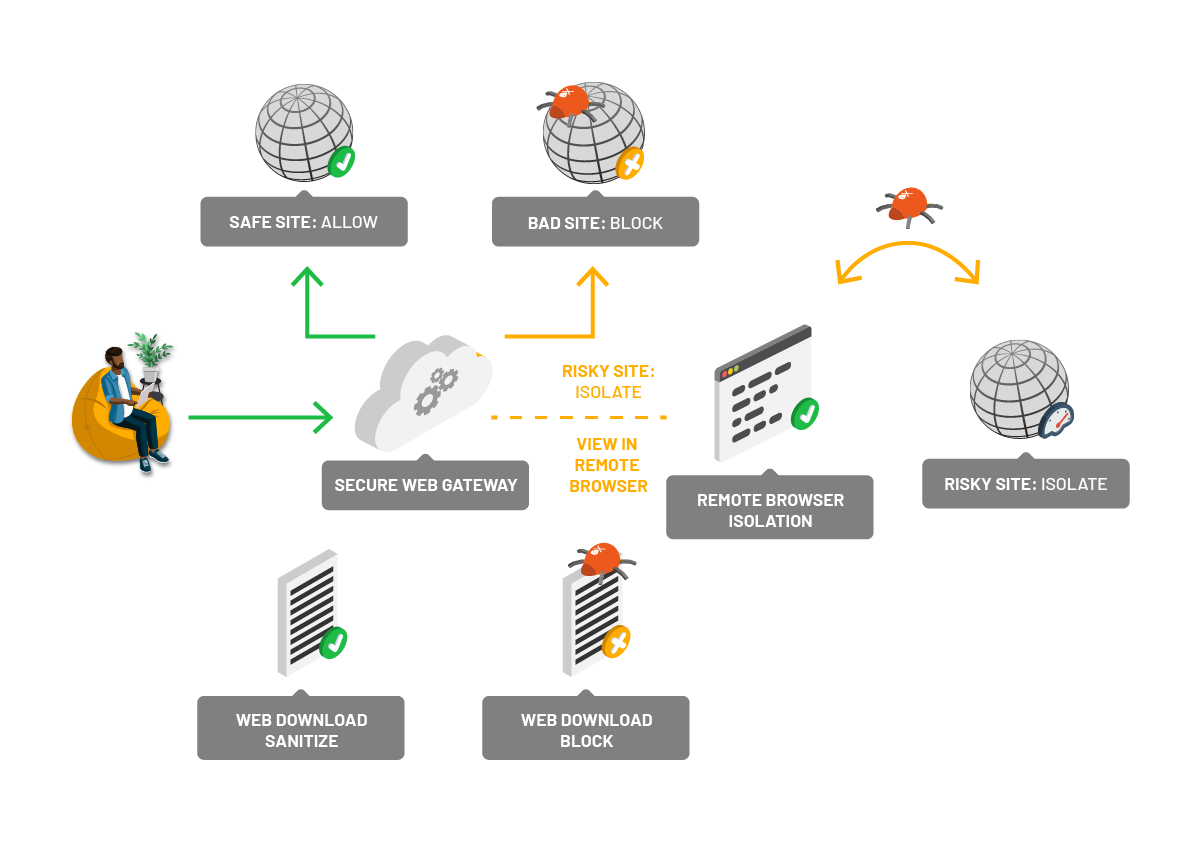
Ericom Web Security
Remote Browser Isolation
SWG with AV
Phishing Prevention
Content Disarm and Reconstruction (CDR)
Ericom Web Security, leveraging the Ericom Threat Intelligence Network, uses integrated secure web gateway (SWG), anti-virus (AV) and remote browser isolation (RBI) to protect users as they browse the web. RBI ensures that malware can’t compromise devices because risky web code never executes in the local browser. Sites launched from URLs in emails can be isolated to stop phishing attacks and prevent credential theft. CDR technology is available to sanitize attachments and web downloads to remove malware in files.
Offer the Ericom Web Enterprise Gateway solution if your customer needs complete SWG proxy capabilities along with RBI and other security controls.
Global Cloud Infrastructure
These Ericom Solutions are delivered on a high-availability elastic cloud infrastructure that scales to deliver the user experience you expect. Always on. Always available. Always secure.
Each Ericom PoP has full-featured, inline security gateways which inspect all traffic and enforce each organization’s specific web, application, data, and network security policies at the edge, where users are connecting to apps and resources. Policy enforcement is user-based and remains consistent regardless of location.
Redundancy is built into every layer of the Ericom cloud platform, from servers to data centers to the connections between them, and both within and across locations. Load balancing and high elasticity deliver a consistent user experience, and the platform’s no-downtime simultaneous update system delivers 99.999% uptime for Ericom customers.