What is Role-Based Access Control?
A Comprehensive Guide To Role-Based Access Control (RBAC)
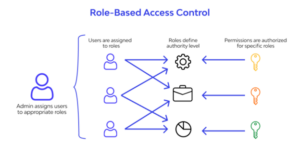
Role-Based Access Control (RBAC) is a security system that defines and manages access permissions to resources based on a user’s role within an organization. It ensures that individuals can only access the information and perform the actions necessary for their specific job functions.
What is Role-Based Access Control?
Role-Based Access Control (RBAC) is an access control model that restricts network access based on the user’s role in the organization. It is a common model used in information security and authorization management. In RBAC, access permissions are associated with roles, and users or system entities are assigned to specific roles based on their job responsibilities and functions within an organization. Each role is granted a set of permissions that define what actions or operations users with that role can perform. For example, a manager might have permissions to approve or reject expense reports, while a customer support representative might have permissions to view and update customer information in a CRM system.
RBAC simplifies access management by centralizing and standardizing the assignment and revocation of permissions. It enhances security and compliance by ensuring that users only have access to the resources and data required for their roles, reducing the risk of unauthorized access and data breaches.
A variety of Role-Based Access Control Models are available. These RBAC models provide distinct approaches to structuring roles, permissions, and user assignments, catering to different organizational structures and regulatory requirements.
Role-Based Access Control Models
Role-Based Access Control offers a systematic approach to managing users and their access to resources. This methodology can be implemented as Core RBAC, Hierarchical RBAC, or Constrained RBAC. Each of these models has its unique characteristics tailored to suit various organizational needs.
- Core RBAC: This model emphasizes the fundamental concept of role-based access. Here, permissions are directly linked to roles, and users are assigned to these roles to gain access.
- Hierarchical RBAC: Hierarchical RBAC organizes roles in a tiered manner. Lower-level roles inherit permissions from their superior counterparts, leading to a layered access control structure.
- Constrained RBAC: This model introduces constraints to control the permissions roles can execute. Such constraints could be influenced by variables like time, geographic location, or other contextual factors.
Core RBAC
Core RBAC lays down the foundation for role-based access control systems. It’s the fundamental layer upon which the other two models build. The core tenets of Core RBAC include:
- Role Assignment: For a subject to access a resource, they must either select or be granted a role.
- Role Authorization: The active role chosen or assigned to a subject must have proper authorization.
- Permission Authorization: A subject can access a resource only if that specific action is permitted for the active role they’ve assumed.
Hierarchical RBAC
Hierarchical RBAC operates on the principle of a cascading permission structure. By organizing roles in a hierarchy, it ensures that roles at a lower tier automatically inherit permissions from their parent roles. This model fosters a methodical delegation of access rights, ensuring efficiency and control in larger organizations.
Constrained RBAC
Constrained RBAC introduces the concept of duty separation. By distinguishing duties, it adds an extra layer of security, particularly vital for sensitive operations. This model functions under two main categories:
- Static Separation of Duty (SSD): Here, an individual user cannot be granted roles that are considered mutually exclusive by the organization’s policy. For instance, the same individual can’t both request and approve a financial transaction.
- Dynamic Separation of Duty (DSD): While a user can be a member of roles with conflicting permissions, they can’t exercise both roles simultaneously during one session. This measure is pivotal in enforcing protocols like the two-person rule, where an operation requires authorization from two separate individuals.
How Does Role-Based Access Control Work?
RBAC is a systematic approach to managing and controlling access to resources within an organization. At the heart of RBAC are four primary components: roles, permissions, users (or subjects), and resources.
- Roles: Roles are predefined sets of permissions that determine what operations can be performed. They are usually based on job functions or responsibilities within an organization. For instance, common roles might include ‘guest,’ ‘contributor,’ or ‘administrator’.
- Permissions: Permissions define what actions are allowed on specific resources. These permissions are bundled into roles, which are then assigned to users.
- Users (or Subjects): Users are individuals or entities that require access to resources. In the RBAC system, instead of granting permissions directly to individual users, they are assigned roles which come with a set of permissions.
- Resources: Resources are the assets or data that users need access to. This could include databases, files, applications, and more.
In the RBAC model, users are associated with roles based on their job functions or responsibilities. For example, a ‘guest’ might have limited viewing capabilities, a ‘contributor’ might be able to both view and edit certain data, while an ‘administrator’ has extensive rights to view, modify, and manage virtually all data.
The strength of RBAC lies in its simplicity and structure:
- Instead of granting permissions to individual users, they are granted roles that already have defined permissions. This ensures a consistent access pattern.
- If a user’s job function changes, or if they no longer need access to specific resources, they can be easily removed from a role, instantly revoking the associated permissions.
- Temporarily assigning roles is also a feature of RBAC. This ensures that users can have “just in time” access for specific tasks, but once the task is completed, the temporary permissions are revoked.
By following the RBAC model, organizations can uphold the security principle of least privilege. This principle emphasizes that each user should be granted only the permissions necessary to perform their specific tasks, minimizing potential security risks.
Understanding Role-Based Access Control Through Examples
To thoroughly grasp how RBAC works, let’s explore some examples and analogies. These scenarios will underscore the dynamics of allocating access based on predefined roles, ensuring a secure and streamlined experience.
Example 1: Soccer Team Analogy
Imagine Maria’s youth soccer team, which includes players, coaches, referees, and a snack bar vendor. In this organizational context:
- Players have permissions to access the locker rooms and the soccer field.
- Referees are given access only to the soccer field to manage the game.
- Coaches are responsible for devising game strategies, maintaining a player roster, and communicating with parents about schedules and performance.
- Snack bar vendors manage the sale of refreshments during matches, handling cash and sometimes even credit card payments.
- The team manager coordinates game schedules, organizes player registrations, collects fees, and ensures everything runs smoothly on match days.
When a new child joins the team as a player, he receives a team jersey, a list of match and practice schedules, and is acquainted with the team’s rules and regulations. The predefined roles immediately determine his rights and privileges, eliminating any ambiguity.
Example 2: Hospital Management System
In a healthcare setup, the roles determine the access to various parts of patient data:
- Doctors are authorized to view complete patient records, prescribe medicines, and order tests.
- Nurses can update patient vitals and dispense medications.
- Administrative staff have the permission to modify patient contact details without delving into sensitive medical data.
Example 3: Corporate Role Access
RBAC’s adaptability shines in corporate environments:
- Software Engineers might have access to platforms like GCP, AWS, and GitHub.
- Marketing Professionals could access tools like HubSpot, Google Analytics, Facebook Ads, and Google Ads.
- Finance Executives would be granted access to financial software like Xero and ADP.
- HR Representatives might access HR tools like Lever and BambooHR.
Each role, be it managerial or contributory, might possess varying access levels within the respective platforms. For instance, a lead software engineer might have higher privileges in GitHub than a junior developer.
Example 4: Dynamic Adjustments in RBAC
Employing RBAC enables flexibility in access management:
- If an employee transitions roles, their permissions can be reallocated based on the new role.
- Users added to a role group inherit the group’s permissions. Upon removal, those permissions are revoked.
- Users might be provisioned temporary permissions, which can be revoked once their task is done.
RBAC tools often include various designations:
- Management Role Scope: Defines the objects a role group can manage.
- Management Role Group: Members can be added or removed.
- Management Role: Determines tasks a specific role group can perform.
- Management Role Assignment: Connects a role with a role group.
Furthermore, access types can vary:
- Primary: Main contact for an account or role.
- Billing: Access for one user to the billing account.
- Technical: Users performing technical tasks.
- Administrative: Users performing administrative tasks.
This modular and organized approach ensures that each user has the exact set of permissions they need, adhering to the security principle of least privilege.
Benefits of Role-Based Access Control
RBAC, or Role-Based Access Control, is a method by which organizations can manage and oversee the access to their resources more effectively. Through assigning roles to users, permissions can be systematically distributed, making access more efficient and secure. The primary advantages of employing RBAC include:
- Enhanced Security: RBAC ensures that users only have access to the information and resources necessary for their specific role. This not only reduces the chances of accidental breaches due to unnecessary access but also limits the potential damage in case of a deliberate attack. By adhering to the principle of least privilege (PoLP), the risk of data breaches is mitigated. Furthermore, the separation of duties ensures that no single user has all-access, further protecting against internal threats.
- Simplified Access Control: With RBAC, user permissions are streamlined. Employees can autonomously access the tools and information they need without going through cumbersome administrative processes. IT departments benefit from reduced administrative tasks, as they no longer have to individually manage access for every user. Additionally, onboarding, offboarding, and other user-related transitions become significantly more straightforward with role-based assignments.
- Improved Compliance: Compliance with local, state, and federal regulations is crucial, especially for organizations handling sensitive data. RBAC provides a clear framework for monitoring and documenting access, making it simpler to prove compliance with regulations such as HIPAA, SOX, SOC 2, and ISO 27001.
- Scalability: As organizations grow, their access control systems need to adapt. RBAC is designed to be flexible and scalable, allowing for easy adjustments and additions of roles and permissions as the organization evolves. This adaptability ensures that even as the company expands, the integrity and efficiency of access management remain intact.
In essence, RBAC promotes a more secure, efficient, and compliant organizational structure, benefiting both the IT teams and the end-users in the process.
Role-Based Access Control Implementation Best Practices
Effective implementation of Role-Based Access Control (RBAC) necessitates a structured approach. Adhering to best practices ensures a smoother transition, minimizes disruptions, and maximizes the potential benefits of your RBAC system. Let’s dive into the essential steps for successful RBAC implementation.
1. Collaborative Planning Across Departments
RBAC implementation isn’t just an IT affair. It requires collaboration across various departments including HR, Security, Executive, and IT. Initiating discussions amongst these departments fosters an understanding of the broader business structure and objectives. This not only paves the way for a smoother transition but also optimizes the outcomes of RBAC initiatives.
2. Develop a Comprehensive RBAC Strategy
- Evaluate Your Current State: Begin by understanding the current access control scenario across systems, data, and processes in your organization.
- Vision for the Future: Define where you aspire to be. Whether you aim to automate provisioning or seek better control over applications holding sensitive data, pinpointing your desired outcomes is crucial.
- Identify Gaps: Acknowledge areas of improvement, whether they relate to authentication models, compliance needs, or any other discrepancies that warrant the shift to RBAC.
3. Take Inventory of Your Systems
Document every resource, service, or application that requires access control. This could range from emails and cloud apps to customer databases and shared folders.
4. Analyze Your Workforce
Collaboration between IT, HR, and executive leaders simplifies this process. Begin by classifying your workforce into roles according to shared access needs. However, be cautious of over-segmentation. The key is to maintain security without impeding innovation. Adopt a two-tiered method:
Top-Down Analysis: Have business managers design roles in alignment with company objectives while addressing the functional access necessities of each role.
Bottom-Up Analysis: Simultaneously, IT should delve into understanding user behaviors and access patterns to further refine role definitions.
5. Define and Map Roles
Merge the insights from your workforce analysis with the resources in your inventory. Utilize the principle of least privilege to determine the access each role should have. For instance, a Basic User role might have access to email and Slack, while a Hiring Manager could be granted read/write permissions to an employee database and professional people management apps.
6. Establish a Governance Structure
Beyond just defining roles, it’s paramount to set up a governance mechanism to oversee them. Clearly document:
- Performance metrics.
- Risk management strategies.
- Guidelines for periodic role evaluations.
- Responsibilities regarding role maintenance.
- Strategies to keep policies current.
7. Assign Roles to Individuals
With your groundwork in place, proceed with the implementation. Assign the designed roles to employees and manage access rights and permissions. In larger organizations, consider a phased approach for RBAC deployment. Commence with a small set of users and progressively expand, making adjustments based on feedback.
8. Embrace the Principle of Least Privilege
Ensure that every user is granted only the minimum access required to fulfill their tasks. Tailor the privileges based on the roles, ensuring each role is tightly defined to prevent unauthorized access or activities.
9. Periodic Review and Updates
Setting up RBAC isn’t a one-and-done project. It requires continuous oversight. Regularly audit the roles and permissions to ensure they align with evolving business needs and objectives. Periodic reassessments ensure that the system remains relevant, efficient, and secure.
When executed meticulously, RBAC not only enhances security but also streamlines business operations. Regular reviews and cross-departmental collaboration are pivotal for the sustained success of any RBAC initiative.
Industry Use Cases for Role-Based Access Control
RBAC plays a pivotal role in ensuring that sensitive data and key processes across diverse sectors are securely managed and accessed only by authorized individuals. Here are some prominent use cases:
- Healthcare (Electronic Health Records): In the healthcare sector, RBAC is essential to protect sensitive patient data. When you consider a medical institution with various departments, not all personnel require access to complete patient profiles. A radiologist might need access to a patient’s X-rays but not necessarily their entire medical history. By implementing RBAC, roles such as ‘Radiologist’ or ‘General Practitioner’ can be established, ensuring that healthcare professionals access only the data they require for their roles, thus maintaining patient confidentiality.
- Finance (Banking Systems & Trading Platforms): The financial sector is fraught with a multitude of transactions and voluminous customer data. Implementing RBAC can streamline and secure access. For instance, in a banking application, a ‘Teller’ role might have permissions to execute basic financial transactions, while a ‘Loan Manager’ role can access and approve loan applications but might not be involved in routine transactions. This structured approach ensures that financial data and processes are safeguarded against any unauthorized access or malicious intent.
- Government and Defense (Military Access Control): National security is paramount. In defense systems, access needs to be granular and highly restrictive. Implementing RBAC can ensure that only those with the appropriate clearances can access certain classified information or systems. A ‘Field Agent’ might have different access permissions compared to a ‘Data Analyst’ or ‘Strategy Consultant’. With RBAC, governments can precisely define these roles and their corresponding permissions, ensuring that classified data remains secure.
- Education (Student Information Systems): Educational institutions manage vast amounts of data, from student grades to staff payroll. By utilizing RBAC, schools and universities can define roles such as ‘Student’, ‘Faculty’, ‘Administrator’, and ‘Parent’. For instance, while faculty can input grades to an academic tracking platform, students would only be permitted to view them. RBAC ensures that student and staff information remains confidential and protected, and is accessed only by the right stakeholders in the manner appropriate for each individual.
It’s worth noting the power of RBAC when combined with modern authentication and authorization systems. Consider the software-as-a-service scenario for non-profits, where roles like ‘Gift Shop Manager’ or ‘Newsletter Admin’ can be precisely defined and assigned. This allows organizations to efficiently manage who can access which module, promoting flexibility without compromising security. Using platforms like Auth0 further simplifies this process, offering businesses the chance to tailor RBAC according to their unique needs and even allowing users to manage their own RBAC, reducing operational costs and enhancing efficiency.
Role-Based Access Control in Ericom Solutions
Ericom solutions enable organizations to leverage Role-Based Access Control as an efficient and effective method of complying with the Zero Trust principle of least-privileged access. Meeting the needs of the decentralized workforce, Ericom Connect is a simple to use remote desktop and application access solution, available as a cloud or on-premise solution, which provides browser-based access to vital IT assets. Centralized management aids IT teams in rapid deployment and policy creation, all under RBAC guidelines. The solution integrates seamlessly with VPNs, employs multi-factor authentication, and utilizes built-in SSL encryption. Additionally, its HTML5 technology transforms legacy applications into online, cloud-ready formats.
Ericom web security solutions leverage RBAC extensively to restrict user access to only the resources, applications and data they need for their work in keeping with Zero Trust least privilege principles. RBAC may be applied to restrict activity within a SaaS, web or private app to read-only, or limit what a user can download or copy from a site. Clientless Ericom Web Access Isolation enables RBAC to be enforced for users logging on via unmanaged devices.
Modern enterprises navigate the benefits and security challenges of Software-as-a-Service (SaaS). Unauthorized access via stolen credentials can have dire consequences, with even well-intentioned employees posing potential risks. Ericom’s Clientless Cloud Access Security Broker (CASB) offers granular control, threat mitigation, and robust data security. Seamlessly incorporating RBAC, the solution establishes a secure SaaS environment, proficiently handling permissions and minimizing threats.
In the digital age, Application Access Management (AAM) is a crucial security cornerstone. It governs access based on RBAC’s role-specific permissions. Ericom’s offerings harmonize these tenets, ensuring both safety and user convenience, as showcased in this comprehensive overview of AAM.