Cybersecurity Challenges Midsize Enterprises, Small Businesses Face
by Simon Moran
Posted on November 2, 2021
Want to interview Simon?
Contact
Of course, “the market” on which most are focused comprises the large, deep-pocketed enterprises that can afford to rip-and-replace complete security stacks and have sufficient IT staff and consulting budgets to take on large projects.
For small and midsize organizations, the picture is a little less rosy. The move to remote work, increasing dependence on cloud computing and storage, and the rapid increases in cyberattack frequency, cost and severity have left them exposed. Yet few have the budget for an end-to-end overhaul of their security stack, and even fewer have the IT human resources needed to manage the process.
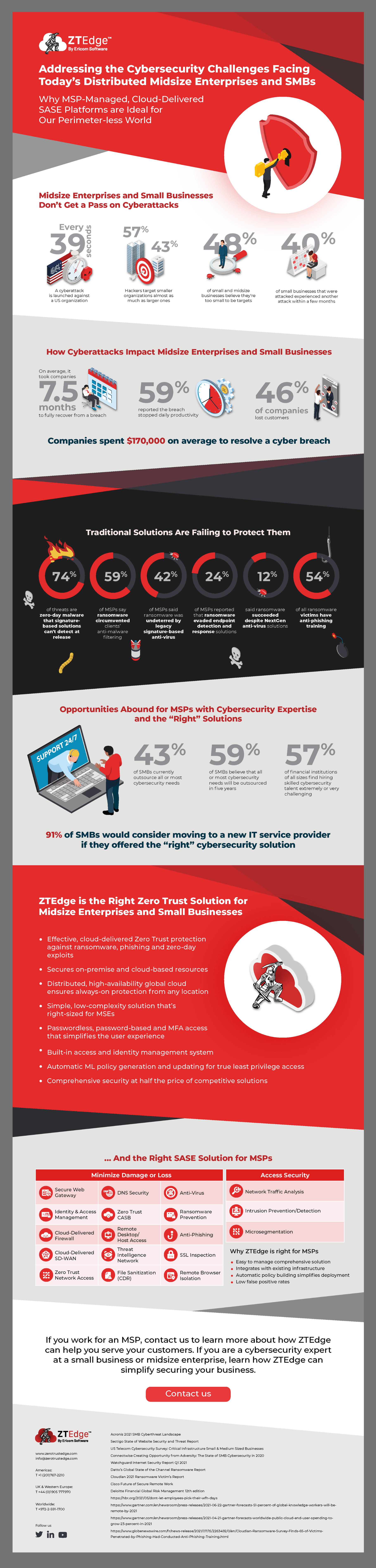
In our most recent e-book, “Addressing the Cybersecurity Challenges Facing Today’s Distributed Midsize Enterprises and SMBs”, we’ve looked at the challenges faced by midsize enterprises and small organizations and came up with some ideas that can help. This short infographic summarizes some of the main points. Hope you find this information useful!
About Simon Moran
Simon manages Ericom global business development and technology partnerships. Previously, as VP Cloud Security at Symantec Corporation, he focused on enabling next gen solutions for Cloud Infrastructure deployment. Along with a unique balance of sales, management and technical skills, Simon has over 34 years of software experience at the world’s largest and most successful software companies including Blue Coat, Oracle, SAP, and Software AG, and over a quarter century of experience in Enterprise Application sales of Security, Customer Experience and Supply Chain software.Recent Posts

Air Gapping Your Way to Cyber Safety
Physically air gapping enterprise networks from the web is a great way to protect operations, keep data safe … and squelch productivity. Virtual air gapping is a better approach.

Motion Picture Association Updates Cybersecurity Best Practices
The MPA recently revised its content security best practices to address, among other challenges, the issue of data protection in the cloud computing age.

FTC Issues Cybersecurity Warning for QR Codes
QR codes on ads are a simple way to grab potential customers before they move on. No wonder cybercriminals are using QR codes, too.