Ericom’s Innovative Isolation-Based Products
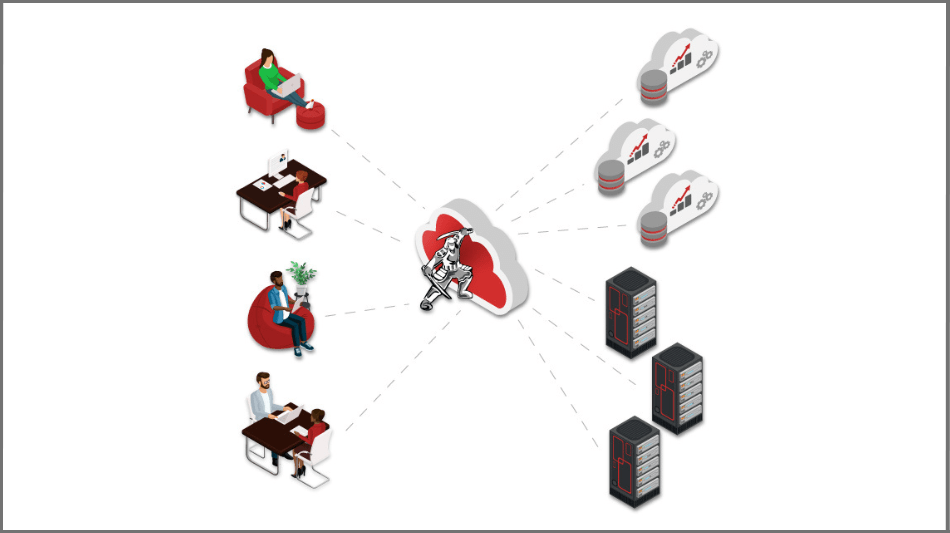
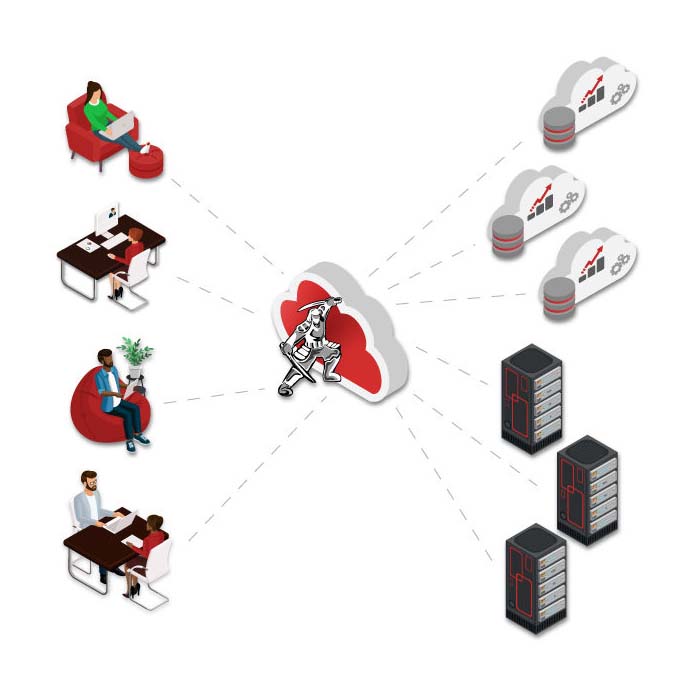
Remote Browser Isolation (RBI) delivers more effective security in many critical Security Service Edge (SSE) use cases.
With clientless RBI, organizations get better protection and a simplified experience for users as they access the web, SaaS applications, and private corporate applications, regardless of where they are located.
Ericom Isolation-Based Products
Web Application Isolation
Clientless ZTNA solution that simplifies secure access to web/cloud apps, even from unmanaged/BYOD devices.
Virtual Meeting Isolation
Enforce data-sharing controls for groups collaborating in meeting applications like Zoom, Teams and Google Meet.

Instant Messenger Isolation
Protecting devices and networks from malware, ransomware, and other exploits hidden in IM web client traffic.
Isolate web and cloud apps to protect them from unmanaged device and BYOD access risks
Access and Data Sharing Controls
Data Loss Prevention
Malware Scanning
Credential Theft Protection
Ericom Web Application Isolation (WAI) is a clientless Zero Trust Network Access (ZTNA) solution that allows organizations to fully control access from unmanaged and BYOD devices to their applications and data. User-level policies determine who can access specific apps and how they interact with corporate data, with no need to install anything on devices.
- Block file uploads/downloads
- Sanitize uploads to prevent the injection of malware
- Scan downloads with DLP to prevent data exfiltration
- Limit/disable cut and paste functions (clip-boarding) to protect data
- Present apps in “read-only” mode (no free-form text updates)
- Prevent apps data from entering an unmanaged device browser’s cache
- Enforce IP-based access control (only permit access through WAI)
- Turn web applications “dark” to attackers and unauthorized users
Ericom WAI is a simple, innovative way to protect BYOD employees and onboard 3rd party contractors in minutes while ensuring the correct data and access security controls are in place for them regardless of which SaaS or Web Apps they need to access.

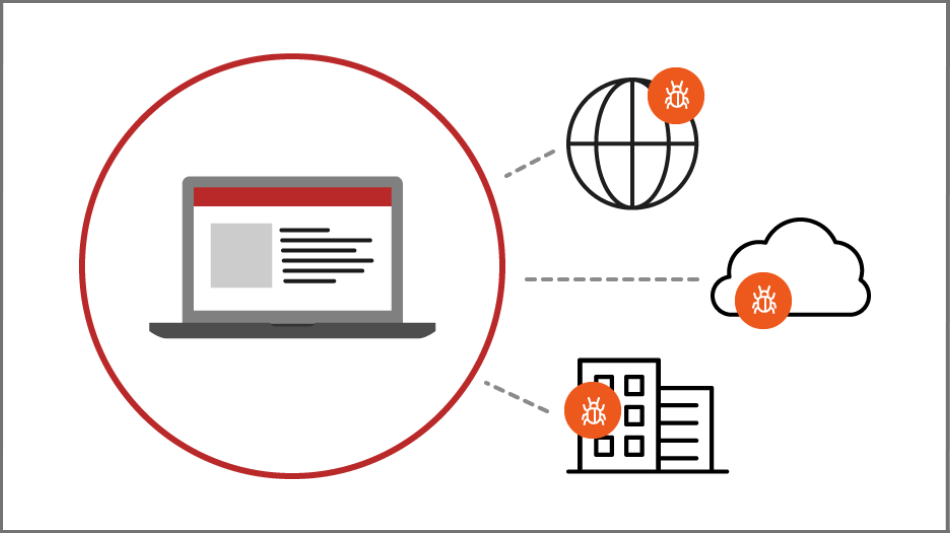
Air-Gap Devices from Malware
Ericom Remote Browser Isolation renders website content in virtual browsers sealed in cloud-based containers.
Only safe rendering information is streamed to users’ regular web browsers, providing a natural, fully interactive user experience, while safeguarding devices and networks from malware hidden on websites – even advanced zero-day ransomware.
ZTEdge Web Isolation even secures end-to-end encrypted traffic in apps like WhatsApp Web, blocking malware and securing data.
Control data sharing for teams collaborating in virtual meeting applications
Isolate Web Portals
Cloak IP Addresses
Restrict Content Sharing
Prevent Intrusions
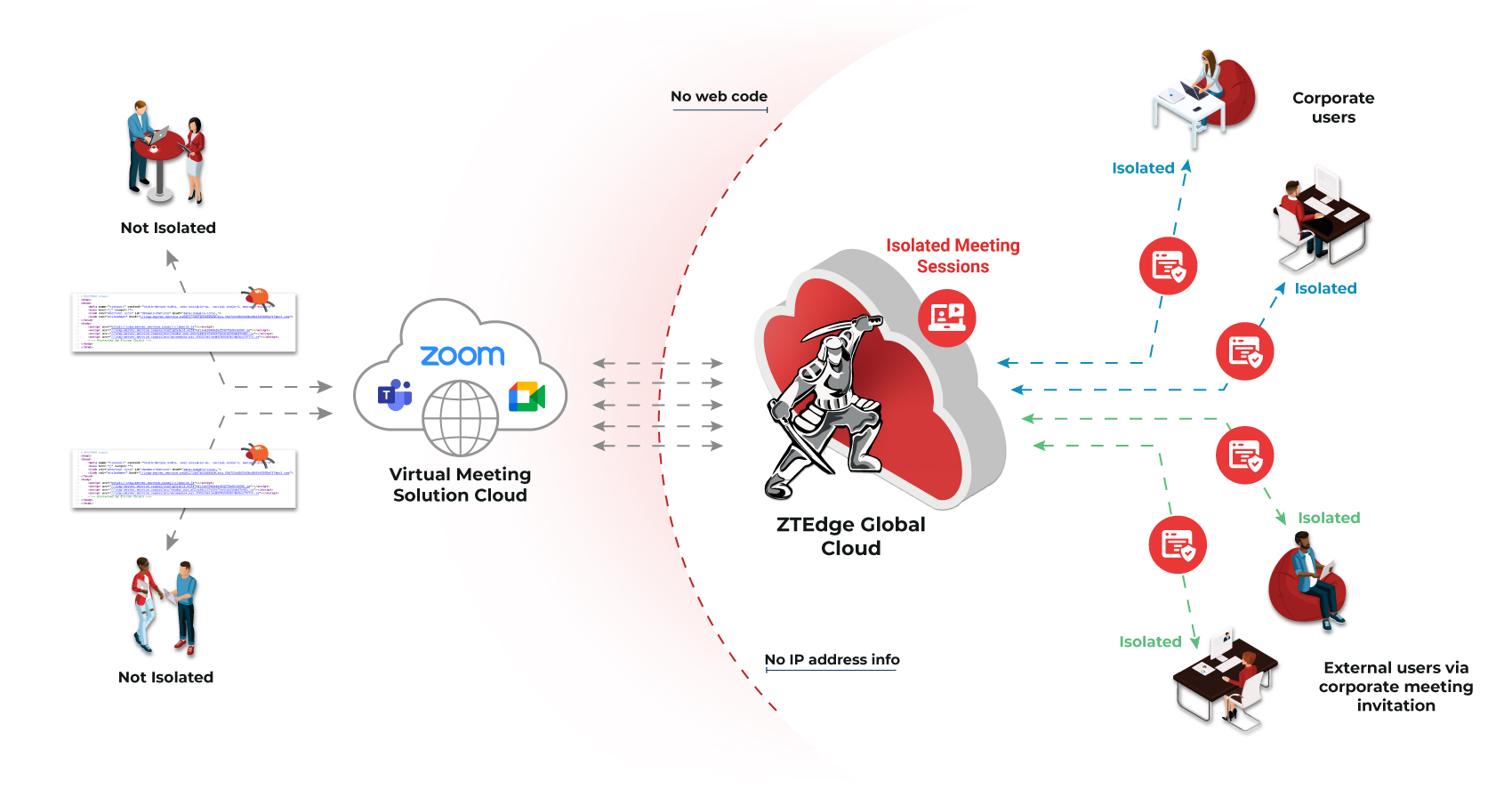
Ericom Virtual Meeting Isolation (VMI) is a patent-pending solution that preserves all Zoom, Microsoft Teams, and Google Meets virtual meeting functionality while protecting organizations from potential data loss by controlling what data and video can be shared by each meeting participant. VMI supports the web portals of virtual meeting solutions and requires no agents or software to be deployed on devices.
Ericom VMI renders the web portals of apps like Zoom in remote, isolated containers in the cloud. This approach delivers a standard virtual meeting experience for users, while empowering IT and Security teams with a number of powerful security controls:
The virtual meeting activity of each participant can be controlled:
- Limit who can share screens or use cameras and microphones
- Determine who can upload and share files
- Select which users can engage in the chat box
- The IP addresses of connecting endpoints are not exposed
- Any web links shared in chat will be rendered in isolated environments ensuring that malicious sites/links do not compromise endpoints
- File uploads/downloads can be scanned for malware with CDR or data loss with DLP
- Prevents unauthorized, malware-enabled recording of virtual meetings
Protect your organization from malware or data loss in end-to-end encrypted chat/messenger applications
Decrypt Messages
Block Malware
Prevent Data Loss
Protect Credentials
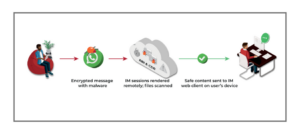
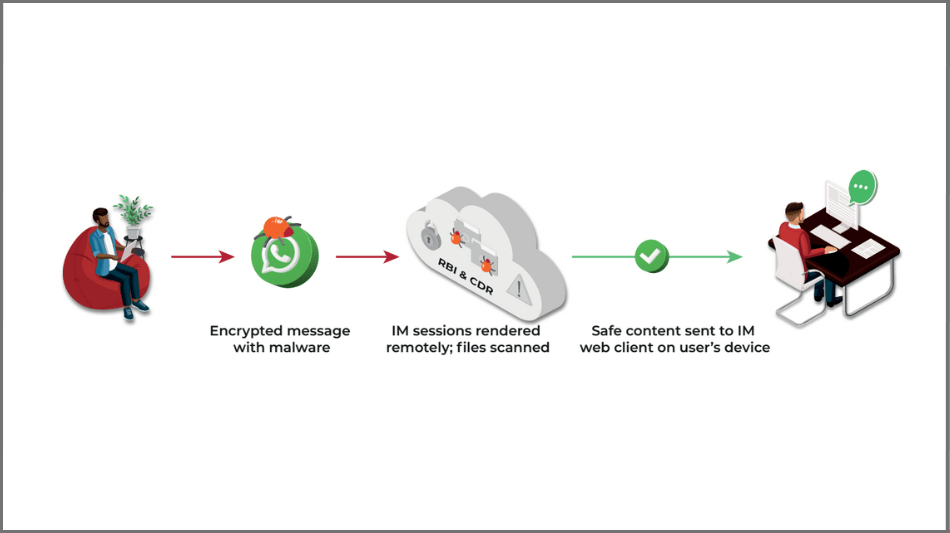
Instant Messenger (IM) web clients, including the wildly popular WhatsApp Web, are a great productivity tool for users – which is why they love them. But their end-to-end encryption approach creates a huge blind spot for most security stacks. ZTEdge Instant Messenger Isolation solves this problem, by protecting endpoints and networks from malware, ransomware, and other exploits that can be hidden within open chats on IM web clients.
With ZTEdge, all instant messages received on endpoint browsers are opened and unencrypted in isolated containers in the cloud, using remote browser isolation (RBI) technology. To protect your organization from malware hidden in files attached to IMs, the solution applies content disarm and reconstruct (CDR) to all attachments. Within the isolated container, files are downloaded, examined for malware and, if necessary, disarmed. The files are then reconstructed with (desired) native functionality intact and delivered to endpoints.
In a similar fashion, all outbound messages can be scanned using Ericom’s Cloud Data Loss Prevention (DLP) to enforce policies on what data may be shared, how and by whom, as well as which data is protected. It protects organizations from IM-enabled malicious exfiltration of sensitive content, deliberate (but non-malicious) sharing, and accidental data loss.