What is Microsegmentation?
Improving Network Security by Reducing the Attack Surface

How Does Microsegmentation Help?
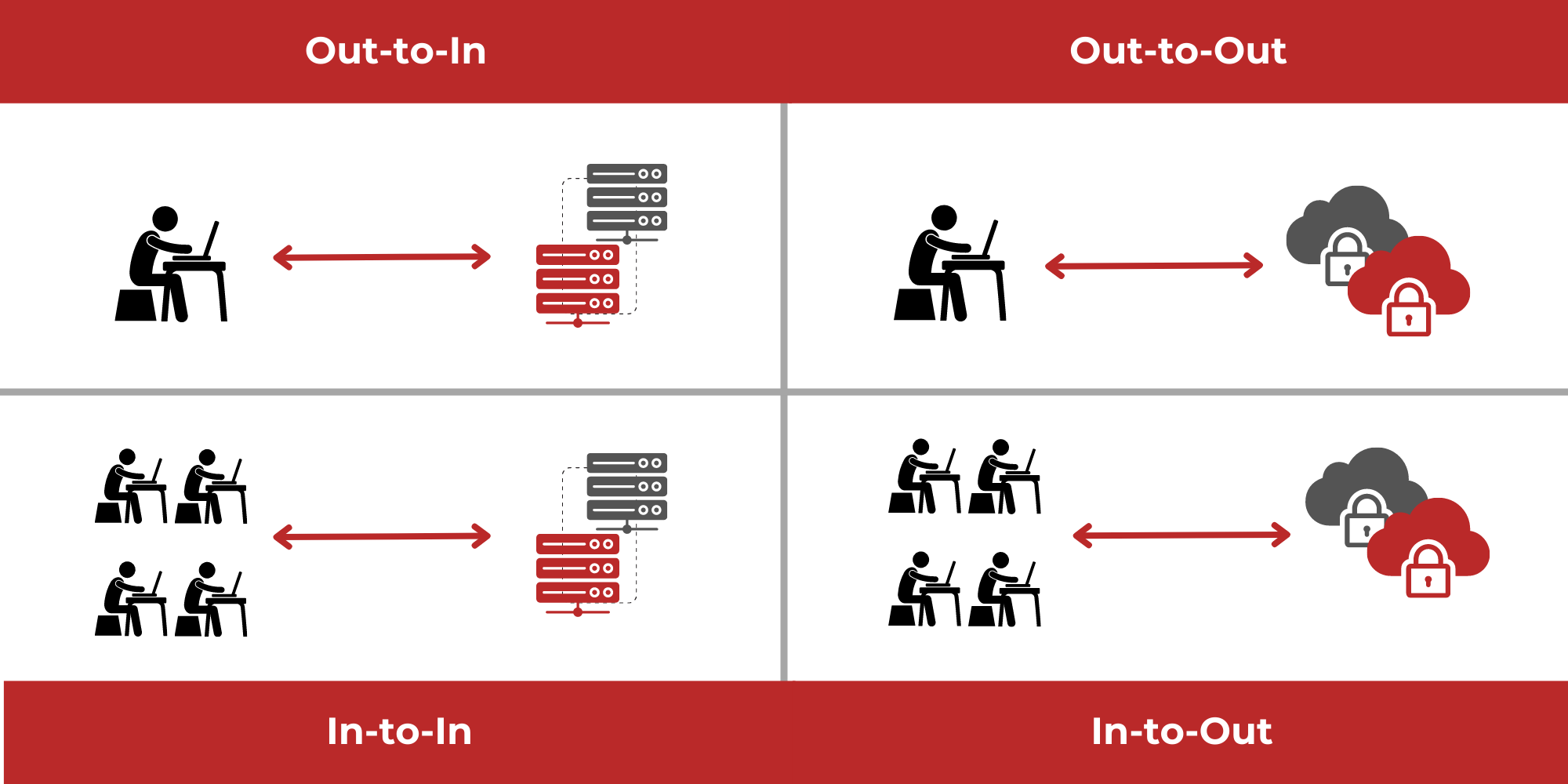
In the traditional networking model, a great deal of effort goes into securing endpoints and connections to the public internet, which form the perimeter where an internal network interfaces with the outside world. Firewalls are designed to protect the internal network – and its sensitive data – from threats coming from the internet or other external sources. Traffic inside the firewall has traditionally been, by definition, considered “safe.” The problem with this model is that once a cybercriminal manages to breach the firewall, they can freely move around the network and cause a lot of damage. This type of perimeter-based model is like a castle with a moat – having the moat and drawbridge up may protect you from outside attackers, but it does nothing to protect you against a malicious character who is already within the castle walls.
Microsegmentation helps by creating a lot of “small castles” instead of one big one. If a hacker manages to breach your firewall, they don’t have access to everything in your datacenters and cloud environment – they only have access to one small segment. The attack surface is reduced, the damage to the cloud and datacenter is contained to a vastly smaller footprint, and regulatory compliance is easier to maintain.
The typical datacenter has a number of interconnected servers. Until recently, microsegmentation has focused on limiting damage to servers by restricting movement between servers on a network. More modern approaches are much more granular, using policy-based microsegmentation to limit user access to only the data or apps that they need, and preventing users (or hackers who manage to get in) from accessing resources they do not have permission to use, creating many tiny secure zones. This type of movement within the “castle,” whether from server to server or app to app is known as “lateral movement” or “East-West” traffic, as opposed to “North-South” traffic in and out of the datacenter, and microsegmentation is designed to restrict it.
Changes in the Business Environment Increase the Importance of Microsegmentation
For several years now, there has been an increasing trend to remote work. The coronavirus pandemic accelerated this trend sharply, with millions of workers suddenly accessing corporate networks remotely. Each additional connection represents an additional vulnerability, another potential route for penetrating the firewall-based perimeter defense. This increases the need for microsegmentation, which can minimize the attack surface, reducing the potential for damage if user credentials are compromised and hackers get into the network.
Many companies have adopted a more collaborative business model, with trusted third parties, as well as employees, being granted access to corporate data centers. It’s especially important that these third parties are only permitted to access the corporate network resources for which they have been approved and that they need to know or work with.
Most businesses are now working in a cloud environment, or a hybrid cloud environment, which makes the concept of a firewall-driven perimeter defense largely obsolete. If an individual workload isn’t even hosted in your own data center, your firewall is not going to provide protection (although hopefully your cloud provider’s does), and a different approach is required.
Implementing Microsegmentation
Network segmentation is not a new concept; companies have been doing it for years to achieve regulatory compliance and network security. Many companies have also already moved to a system of “least privilege” under which they only grant users access, or the level of access, required for each piece of data (in other words, if a user only needs to be granted access to read something, they are not given rights to write to that file). Microsegmentation is a type of network segmentation that takes the least privilege concept and extends it more broadly in datacenters and cloud or hybrid cloud environments.
There are different ways to implement microsegmentation. Experts recommend against using a network topology or address-based approach to security, partly because of the administrative overhead involved.
Microsegmentation is more efficiently implemented by developing a set of security policies and applying them via software security controls to individual secure zones.
Effective microsegmentation takes things down to the process level. The whole point of microsegmentation is to block attackers from being able to engage in not just North-South movement into the datacenter from outside, but also East-West, lateral movement within the datacenter and cloud environment by accessing permitted ports.
It’s also important to make sure that microsegmentation security policies are comprehensive. Some companies have suffered losses because they failed to include one-off services in legacy on-premises datacenters in their microsegmentation scheme. Network security is only as strong as the weakest link.
Microsegmentation and Cloud Environments
Being software and workload driven, microsegmentation works well in cloud or hybrid environments. Most businesses now operate in a hybrid cloud setup, with some functions on servers in the corporate datacenter, and others in the cloud. Security controls based on physical infrastructure such as IP addresses don’t work well across cloud applications. With workload level defined microsegmentation the policies and segmentation can be applied regardless of where the application and data are hosted.
Microsegmentation and Zero Trust
The Zero Trust approach to security eliminates dependence on the assumption that users who have been verified and granted network access are safe. It views the world through a suspicious lens and assumes that no one and no thing inside or outside the network perimeter should be completely trusted.
Zero Trust is a network security philosophy; implementation is accomplished through a variety of tools. Microsegmentation has an important role to play – instead of defending a perimeter, the network establishes many limited “micro-perimeters”, making sure to secure them individually. In addition to microsegmentation, traditional tools such as antivirus/anti-malware software and firewalls still have a role to play. Cutting-edge techniques such as Identity and Access Management (IAM), secure remote access, Remote Browser Isolation (RBI), and Security Orchestration, Automation and Response (SOAR) leverage and/or work with microsegmentation to translate these principles into practice.
- IAM encompasses a variety of techniques that are basic to a Zero Trust approach. Stepping up your game on identification by not trusting a user simply because they have a password, and requiring one or more additional forms of identification – i.e. two- or multi-factor authentication – is an obvious application of this “always verify” stance. IAM typically also includes mechanisms for restricting users to resources they need, and tightly control of superusers such as system admins. Data encryption is also typically deployed both for session privacy and to ensure data security.
- With many more workers working remotely in the wake of the coronavirus pandemic, another weak spot in network security can be remote access. Cybercriminals are targeting RDP (Remote Desktop Protocol). Using an advanced virtual computing platform, such as Ericom Connect, can also help, especially since it provides client-less access – no worries about end users not updating their software as they are supposed to.
- Remote browser isolation (RBI) extends the “Zero Trust” concept to websites users might visit. Antivirus and antimalware programs can’t necessarily keep up with new threats in real-time. With RBI all web surfing is done in an isolated, one-time use container on a separate server. If an employee did click on a link that led to some malware, the malware has nowhere to go – it can’t infect either the main server or the end user’s device.
- Security Orchestration, Automation and Response (SOAR) deploys a stack of software programs that collect data on security threats and respond to low-level threats in real-time, automatically and without human intervention.
Conclusion
Microsegmentation is an increasingly common approach for companies seeking to protect their digital assets. By reducing the network attack surface (the portions of a network accessible to an attacker) through the use of “micro-perimeters,” microsegmentation vastly reduces the damage a cybercriminal can do by limiting east-west, lateral movement of unauthorized users from server to server, and from resource to resource.
With security policies that are software-defined and software-implemented, microsegmentation is well suited to the data centers and cloud environments in which businesses of all sizes operate today.
A full Zero Trust security approach is the best way to secure your network. Microsegmentation is an essential element of this approach.
