Protect users while they connect
from their mobile devices
Ericom offers agent-based and agentless approaches that allow you to enforce security policies to protect mobile users, and the networks they access, from threats.
Protect Mobile Users as they Access the Web
Agentless approach to securing web browsing from mobile devices
Enforce Acceptable Use Policies
Block Access to Risky Sites
Browsers on mobile devices can be configured to route web traffic – through the ZTEdge platform. Administrators configure policies – on a user, group, or device type level – to allow or block access to specific websites
Without the need for an agent on the mobile device, Ericom’s DNS-based security controls prevent employees from visiting websites that violate corporate acceptable use policies (AUP) or that may compromise network security.
Ericom leverages threat intelligence from multiple sources to assist IT security teams, allowing them to use website category and risk information to create robust website access policies.

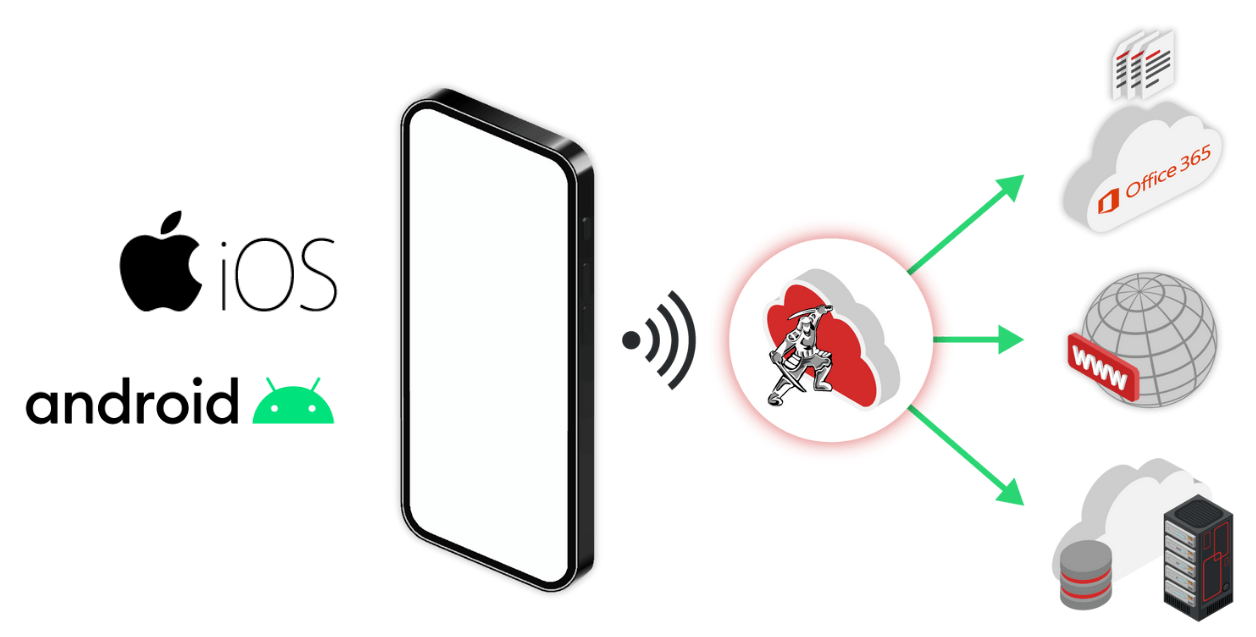
Protect Mobile Users When They Access Apps, Data and Networks
ZTEdge mobile device agent enables the full protection of the SASE platform
Protect Users
Protect Apps & Networks
Protect Data

With the ZTEdge client installed on mobile devices, your organization can enforce strong security policies across mobile device traffic to the web, cloud, and private applications.
Web traffic is directed through the ZTEdge cloud where security policies for internet traffic by SWG and CASB capabilities. Security screening such as anti-virus checking, data loss prevention, phishing prevention, checks on file downloads, and SaaS application access controls helps to protect users and their devices.
Access to applications, both cloud applications and those located in datacenters, is managed via the ZTEdge IAM and ZTNA solutions, ensuring that authenticated users are allowd access to only the specific applications they are permitted to access from their mobile devices. Of course, all mobile traffic is monitored and logged for full ZTEdge visibility and reporting.

