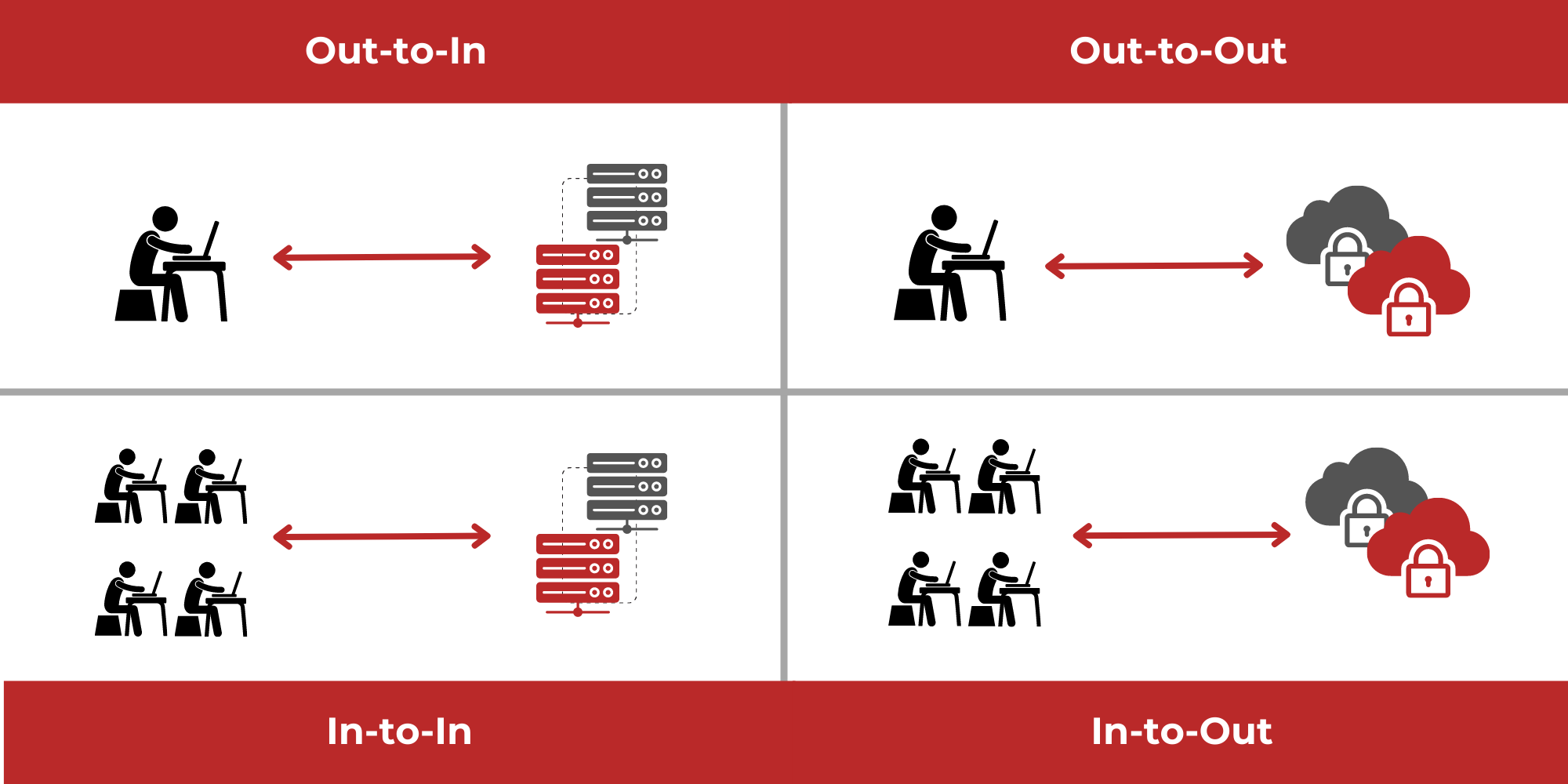
What is Web Application Isolation?
How does web application isolation work? How does it provide protection for both applications and their users?
 Web application isolation is a cybersecurity solution that focuses on providing protection from web-based threats that target web applications.
Web application isolation is a cybersecurity solution that focuses on providing protection from web-based threats that target web applications.
Protecting web applications is an important use case of remote browser isolation (RBI). The technology behind web application isolation is the same technology that is used for remote browser isolation, only used in reverse. Instead of preventing hackers from targeting and breaching a network through endpoint web browsers, it prevents hackers from being able to target and breach corporate web or cloud applications, and provides comprehensive, two-way protection for both the application and its users.
The technology behind web application isolation
To explain the way web application isolation works, let’s begin with a brief description of the technology behind it – remote browser isolation technology.
Remote browser isolation technology allows users to browse the web safely. Without remote browser isolation in place, users that browse the web are vulnerable to a large range of threats, which use the web browser as an entry point. These threats enable hackers to infect the end user’s computer, and use it to access an organizational network, after which they can move laterally through the network and launch a full-fledged cyberattack. However, with a remote browser isolation solution, web-based threats can’t reach the end user’s computer at all, so there’s no chance of infection. Here’s a breakdown of how it works:
- When a user first opens their web browser, or opens a new tab, all active code from the website being visited is run inside a virtual container, away from the endpoint, in the cloud. This means that any code, whether it is malicious or otherwise, cannot access the endpoint in the first place, rendering any malicious web content that is embedded in the webpage as completely harmless to that visitor.
- The end user continues to browse the web through their usual browser, via safe, clean rendering data, for a seamless interactive user experience.
- Once the web browsing session is over, or the current tab is closed, the virtual container is destroyed, along with all of the code inside it, so anything malicious can’t present a risk in the future.
Remote browser isolation uses a Zero Trust approach to information security, by treating all active code from the website as a threat, whether or not it’s actually malicious. This provides protection from even the latest, unknown web-based threats. These ‘zero-day’ threats are often able to evade detection by traditional solutions, such as antivirus solutions, which rely on a database of known signatures to detect threats.
Learn About Remote Browser Isolation
How does web application isolation actually work?
When it comes to web application isolation, the same web isolation technology used by RBI is used to cloak web-exposed attack surfaces, such as web application code or exposed APIs. All active code belonging to the application is run away from the application itself, in a virtual container.
Usually, a hacker would search through the source code of an application in order to find vulnerabilities that can be exploited. With web application isolation, the only kind of source code that will be visible to a hacker is the source code related to the web isolation solution. Due to this, it’s impossible for hackers to find an entry point through which they could breach the secure web application and gain access to corporate servers or systems. There are other benefits of this cloaking too:
- A web application cannot be cloned in order to create phishing sites or similar. These cloned sites can present a significant security risk to application users, who may fall for the exact copy and enter their private details without realizing it is not the real application.
- Competitors cannot view or copy any of the application source code for their own use, allowing the application owners to retain competitive advantage.
Just like RBI, using a web application isolation solution doesn’t affect the user experience. The secure web application is still completely functional and interactive, yet behind the scenes, web isolation technology is keeping the application secure.
When web application isolation solutions are used, the application is often also protected through authentication. When the user first visits the application, they are prompted to authorize themselves, such as through the use of a username and password. Only after authorizing themselves successfully are they able to access the application. This helps prevent unauthorized access by hackers, acting as an extra layer of protection.
How does web application isolation protect application users?
Web application isolation provides two-way protection. In addition to protecting web applications from being targeted by cybercriminals, it also protects the application users. Both authorization and the isolation technology itself ensures that hackers cannot breach the application and embed any malicious code in it, which protects end-users from phishing attempts, malware infection, and other application-based attacks.