Learn from Ericom experts why isolation-based security is the only approach to address more advanced zero-day cyber exploits that current detection-based approaches can’t guard against.
- A 20% discount on our cybersecurity solutions is available to current Ericom customers who register for any of our webinars.
- Please share this information with colleagues who are responsible for exploring and assessing security solutions.

Remote Browser Isolation – Targeted
Does over-blocking of uncategorised websites cause user frustration and burden your IT and helpdesk staff?
Does it create tension between IT security and business users?
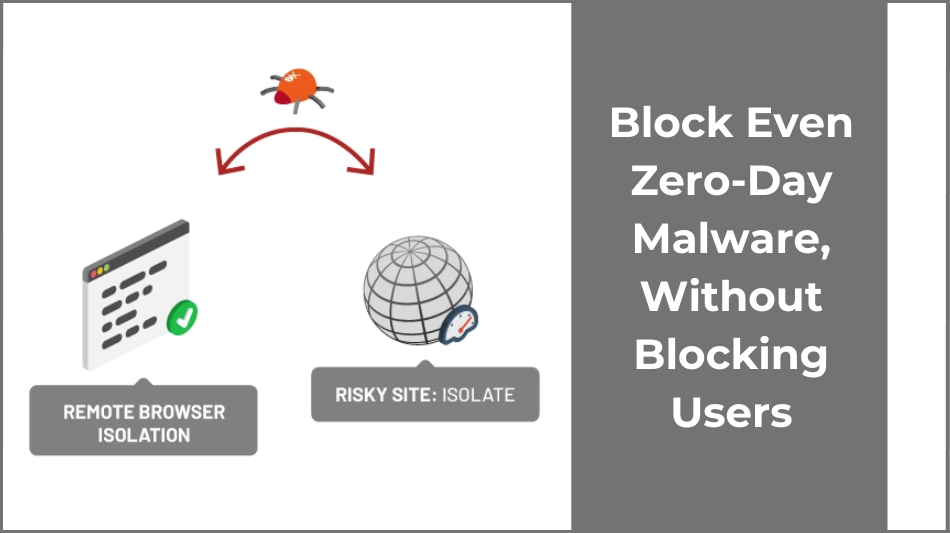
Remote Browser Isolation – Full
Are users in your organisation who deal with confidential and sensitive data getting phished despite your use of so-called “security solutions” that claim to stop phishing?
Virtual Meeting Isolation
Is your organisation restricting or blocking the use of Zoom, Teams, Webex, and other essential virtual meeting applications
due to the well-documented security risks they pose?

Web Application Isolation
Does your organisation need to allow corporate application access to BYODs and unmanaged devices used by your employees, customers, business partners, and contractors, where the inability to control or manage these devices cause a security risk?

#1: Remote Browser Isolation – Targeted
Tuesday, April 18 @ 10 am BST
Enhance your current web filtering solution to provide isolated, air-gapped access to uncategorised and higher-risk websites and downloads, rather than completely blocking access.
Does over-blocking of uncategorised websites cause user frustration and burden your IT and helpdesk staff?
Does it create tension between IT security and business users?
In this webinar, you will learn how RBI can enable secure, air-gapped access to such sites in isolation, so that users can seamlessly access these sites via isolation, removing any potential risks posed by some uncategorised, risky sites.
#2: Remote Browser Isolation – Full
Wednesday, April 19 @ 10 am BST
Address the risks of both known threats and unknown zero-day exploits that your current anti-virus, malware, and email security solutions don’t capture.
Are users in your organisation who deal with confidential and sensitive data getting phished despite your use of these so-called “security solutions” that claim to stop phishing?
In this webinar, you will learn why these solutions are failing to detect modern-day attacks, and how Ericom’s unique prevention approach can mitigate even zero-day phishing attacks, from the second the attack is launched. Ericom’s RBI not only air-gaps your networks, applications, and data from the dangers of the internet, but also enforces browser controls to stop users from entering their login credentials on unknown sites. This stops credential theft and data exfiltration, and blocks malware embedded in malicious documents from compromising your systems and data.
#3: Virtual Meeting Isolation
Thursday, April 20 @ 3 pm BST
Protect against the known vulnerabilities of using video conferencing applications, and control the use of screen sharing, uploads and downloads via these applications.
Is your organisation restricting or blocking the use of Zoom, Teams, Webex, and other virtual meeting applications
due to the well-documented security risks they pose?
In this webinar, you will learn how Ericom’s VMI solution air-gaps your virtual meeting calls to remove the risks of being compromised, while giving the user a completely seamless and native experience.
#4: Web Application Isolation
Friday, April 21 @ 10 am BST
Protect your corporate web applications from the risks of users on unmanaged devices and from hackers gaining access through the growing number of vulnerabilities that are appearing regularly.
Does your organisation need to allow corporate application access to BYODs and unmanaged devices used by your employees, customers,
business partners, and contractors, where the inability to control or manage these devices cause a security risk?
In this webinar, you will learn how WAI can:
- allow safe, clientless ZTNA access to your applications from risky, untrusted and potentially unsafe devices without the need to install any software on those devices
- prevent hackers from accessing your web applications through these vulnerabilities, even before they are discovered.
One of the biggest challenges to security architects is how to give unmanaged devices secure access to your corporate applications and data, without having to install agents and risking the integrity of your applications. By setting granular security policies to protect the apps against unsafe uploads and protect your sensitive corporate data from being stored on untrusted devices, users can seamlessly access your corporate web applications.
